Introduction
Open Redirection Attacks are more than just another item on the list of possible web application vulnerabilities; they are a grave security threat that can lead to devastating consequences. Understanding and mitigating these vulnerabilities is an essential skill for any web developer or security professional. In the following sections, we will dissect open redirection attacks, how they work, and, most importantly, how you can secure your applications against them.
Understanding Open Redirection Attacks
Definition and Explanation
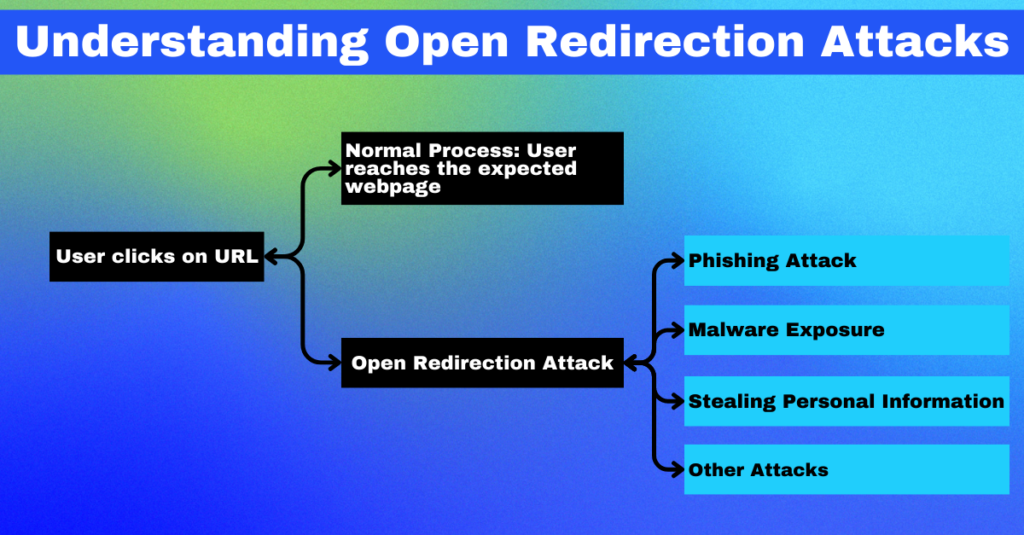
At their core, Open Redirection Attacks are a type of security vulnerability that take advantage of web applications that fail to validate and sanitize input URLs properly. Attackers manipulate URL parameters to redirect users from a trusted website to a malicious one. This underhanded maneuver is typically executed by modifying URL parameters, making it a versatile and hard-to-detect threat.
Common Examples and Use Cases
Some common examples of where open redirection attacks can occur include login redirections, where the attacker can manipulate the ‘return_url’ parameter after a login process to point to their malicious site. Similarly, profile links can also be targets, where attackers modify the profile link to redirect users to an attacker-controlled site instead of the intended profile page. These are just two examples, and the possibilities are as varied as the number of websites on the internet.
Exploitation by Attackers
Crafty attackers can leverage open redirection vulnerabilities to their advantage in numerous ways. They can use it to mount phishing attacks, direct unsuspecting users to sites filled with malware, or use the trusted site as a launchpad for launching other types of attacks. The redirection is just the tip of the iceberg; the real danger lies in what the attacker does once the user is on their controlled site.
The Impact of Open Redirection Attacks
Security Risks
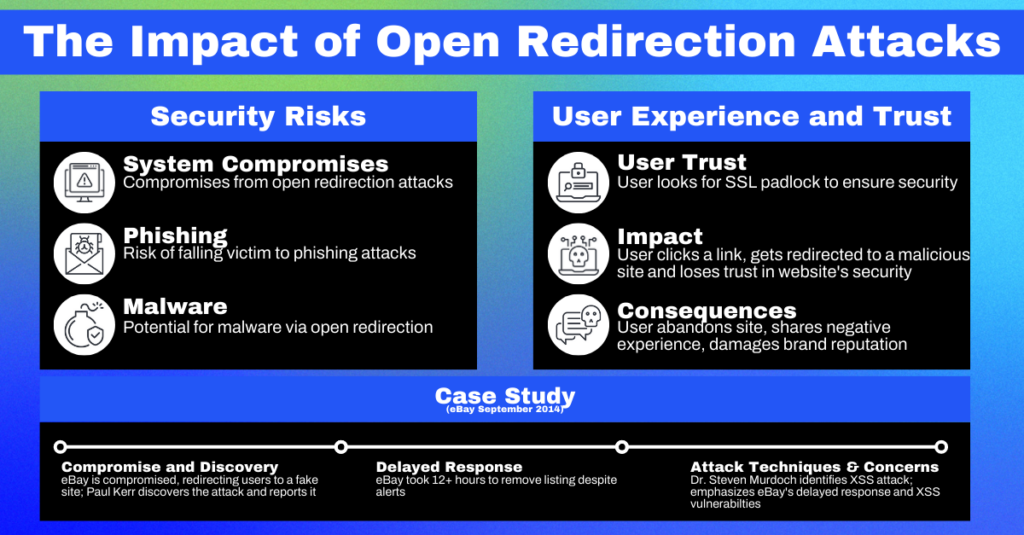
The security risks associated with open redirection attacks are manifold. At the very least, they can expose users to phishing, malware, or stolen personal information. In the worst-case scenario, they can also lead to system compromises if the redirected site exploits browser vulnerabilities. They can also be used with other vulnerabilities, like Cross-Site Scripting (XSS), to escalate the potential damage.
User Experience and Trust
The potential impact on user experience and trust is not to be overlooked. Users trust websites to keep them safe, and when they are redirected to malicious sites, this trust can be irrevocably broken. This can lead to users abandoning the site and tarnishing its reputation, causing significant financial and reputational damage.
Case Studies
Case studies of open redirection attacks abound on the internet. One of the most infamous cases was the open redirection vulnerability in eBay’s website, which attackers used to redirect users to a malicious phishing site designed to steal their credentials. The sheer scale and high-profile nature of this attack serve as a sobering reminder of the potential damage that can be caused by failing to handle redirections properly.
Identifying Potential Open Redirection Vulnerabilities
Common Places
Open redirection vulnerabilities often hide in plain sight. They can be found anywhere a web application uses a URL parameter to determine where to redirect a user. This can include locations such as authentication processes, navigation functionalities, or seemingly harmless features like language selection or theme changes.
Vulnerable Code Example
Consider a PHP application that uses the header function to redirect users based on a redirect_url parameter:
| <?php $redirect_url = $_GET[‘redirect_url’]; header(“Location: $redirect_url”); ?> |
The above code snippet does not validate or sanitize the redirect_url parameter before using it in the header function. This makes it highly susceptible to open redirection attacks.
Detection Tools
Many tools and techniques exist to find potential open redirection vulnerabilities in your applications. These can range from automated security scanners like Qwiet to manual code reviews. Using a combination of these techniques can help you ensure that you’ve covered all your bases.
Strategies and Best Practices to Prevent Open Redirection Attacks
Validating and Sanitizing Inputs
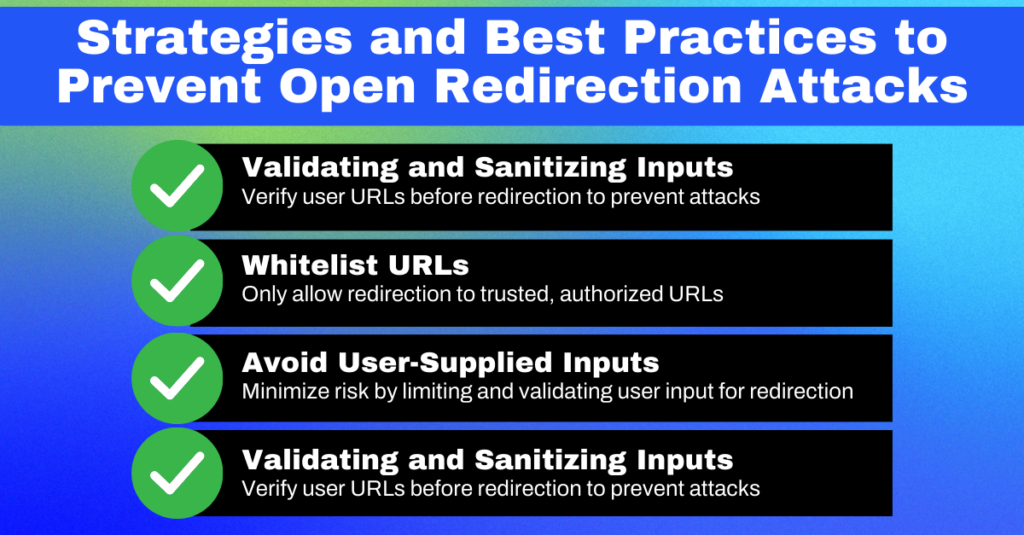
The first line of defense against open redirection attacks is always input validation and sanitation. Ensure that the URL is safe before using it in a redirection. Never blindly trust user input, especially when used in sensitive areas like redirections. Use standard libraries or frameworks that have been thoroughly tested and are widely trusted to perform these operations, as they can save you from many headaches.
Whitelisting URLs
Another good practice to adopt is URL whitelisting. In other words, maintain a list of URLs your application knows and trusts. Only allow redirections to these URLs. This way, even if an attacker can inject a malicious URL, your application will not redirect to it because it’s not on the whitelist.
Avoiding User-Supplied Inputs
The less you rely on user-supplied input for redirections, the safer your application will be. If your application’s functionality allows it, try to avoid using user input to determine redirection destinations. If you must use user input, ensure it’s rigorously validated and sanitized before use.
Security Headers and CSP
You can also improve your application’s security by implementing proper security headers and a Content Security Policy (CSP). These measures instruct the browser on what sources it should trust for different types of content, adding an extra layer of security against various attacks, including open redirection attacks.
Conclusion
Open Redirection Attacks are not to be taken lightly. Understanding these threats and implementing robust preventive and detection measures is paramount in today’s threat landscape. Always embrace good coding practices, secure configurations, and continuous monitoring, and never hesitate to invest in security awareness. Staying ahead of the threats is the key to keeping your applications and users safe.
If you want to take a more proactive approach to reduce the number of potential vulnerabilities in your code base, book a call with our team to get a demo of Qwiet today or take it for a spin yourself.