Abstract
The IEEE 802.11 standard for wireless local area networking (WLAN), commercially known as Wi-Fi, has become a necessity in our day-to-day life. Over a billion Wi-Fi access points connect close to hundred billion of IoT devices, smart phones, tablets, laptops, desktops, smart TVs, video cameras, monitors, printers, and other consumer devices to the Internet to enable millions of applications to reach everyone, everywhere. The evolution of Wi-Fi technology also resulted in the first commercial piloting of spread spectrum, high speed optical communications, OFDM, MIMO and mmWave pulse transmission technologies, which then became more broadly adopted by cellular phone and wireless sensor networking industries. The popularity and widespread Wi-Fi deployment in indoor areas further motivated innovation in opportunistic cyberspace applications that exploit the ubiquitous Wi-Fi signals. The RF signal radiated from Wi-Fi access points creates an “RF cloud” accessible to any Wi-Fi equipped device hosting or supporting these opportunistic applications. Wi-Fi positioning and location intelligence were the first popular opportunistic applications of Wi-Fi’s RF cloud. Today, researchers are investigating opportunistic applications of Wi-Fi signals for gesture and motion detection as well as authentication and security. This paper provides a holistic overview of the evolution of Wi-Fi technology and its applications as the authors experienced it in the last few decades.
1 Introduction
In the last few decades, as we were witnessing the emergence of the “information age” and the third industrial revolution, wireless access and localization played an undisputable role by enabling millions of innovative and popular cyberspace applications to connect to the Internet by anyone, anywhereFootnote 1. These cyberspace applications have had and continue to make a fundamental impact on the way we live, conduct business, shop, access news media, deliver education, transport, care for health, and interact with the world. Today, smart phones, tablets and laptops use wireless technology to support untethered access to information, which is the most essential part of the way we live and work.Footnote 2 Smart cities monitor the environment and cyberspace intelligence is helping us as a society to optimize the way our intelligence contributes to the collective intelligence of humanity, to optimize the efficiency of consuming resources while sustaining life on the earth. The backbone of this third industrial revolution has been the computer and communication industry. The exponential growth in computational speed and the size of memory for information processing and storage has enabled implementation of numerous cyberspace applications that at the same time demand high speed communications and networking of devices, especially with tetherless connections to easily reach the numerous types of consumer devices emerging with the growth of the microelectronics industry at a reasonable cost. Wireless technologies have played an extremely important role in enabling this revolution to take place and to facilitate the access and intelligent processing of information to anyone, anytime, and anywhere.
At the time of this writing we have two different wireless data interfaces to connect a smartphone to the Internet, IEEE 802.11 wireless local area networks, commercially known as Wi-Fi, and cellular mobile data networks. Wi-Fi is the primary choice for smartphones because it can provide a higher data rate and more reliable indoor connections at a lower cost - users typically resort to cellular networks as a second choice. Researchers in next generations of cellular industry believe that as the cellular data rates and cellular costs goes down, the balance may shift to cellular networks because it is available everywhere. However, as of today Wi-Fi is the fastest and most cost-effective way of wireless Internet connectivity, especially in large parts of the world where broadband wired connectivity exists, but the latest 5G cellular technology does not. In addition to smartphones, many other devices like home entertainment systems, environmental monitoring sensors, and security systems connect to the Internet with Wi-Fi, but not necessarily through cellular networks. Wi-Fi brings people, processes, data, and devices, together and turns data into valuable information that makes life better and business thrive [1]. Some companies engaged in Wi-Fi related business resort to artistic illustrations similar to Fig. 1 (adapted from [2, 3]) to relate Wi-Fi to human basic needs using Maslow’s hierarchy of human needs [4], with an additional lowest layer called Wi-Fi. Usually, Maslow’s hierarchy is shown as a pyramid, but to illustrate the crucial importance of Wi-Fi, in Fig. 1 the hierarchy is shown using the inverted version of the common symbol for Wi-Fi signal strength with Wi-Fi as the “most basic” of human needs.
Innovations after the first and second industrial revolution, such as the steam engine, the internal combustion engine, electricity, the telegraph and the telephone, radio, television, airplane, and rockets, had profound impacts on the way we live and have affected many other industries (such as entertainment). However, the Internet, the fruit of the third industrial revolution, enabling the emergence of the “information age”, has had a wider impact on our daily lives. The Internet provides access to unlimited amounts of information in an almost instant manner, anywhere, and that is further enhanced by wireless technologies by allowing devices to be anywhere. Indeed, Wi-Fi is the most popular of the wireless technologies to connect the devices and carry the internet protocol (IP) traffic.
As mentioned above, Wi-Fi is one of two primary wireless technologies that carries IP traffic. The IP traffic includes text, voice, images, and videos that comprises the communication needs in our daily lives and it is a good measure of information exchange on the Internet. A reliable source for measurement and prediction of IP traffic is the Cisco Visual Networking Index: Global Mobile Data Traffic Forecast [5]. Figure 2, adapted from this source, shows the breakdown of this data from Mobile, Wi-Fi and Fixed access in different years. We use their prediction of traffic in 2022 as a measure to demonstrate the role of Wi-Fi in handling IP traffic. The traffic is divided into wireless (Wi-Fi and cellular mobile) and wired (Ethernet) with wireless carrying 70.6% and wired carrying 29.4%. Because of its flexibility of connection, being available anywhere, wireless traffic is more than twice the wired traffic. Fixed devices generate 58% of the traffic and mobile devices generate 42%. Wi-Fi carries 22.9% of the traffic from mobile devices (that also have a cellular connection) and 28.1% of traffic from Wi-Fi only devices for a total 51% of the entire traffic. This means that by the year 2022, Wi-Fi may carry the majority of IP global traffic soaring to reach the unbelievable high value of zettabytes (1021bytes). The reason for the success of Wi-Fi over wired Ethernet, carrying 29.2% of the traffic, is Wi-Fi’s connection flexibility, and the reason for success over cellular, carrying 19.6% of traffic, is Wi-Fi’s higher speed and less expensive connection cost. We use these numbers as a proxy metric to now explain why we need Wi-Fi. This discussion clarifies our “artistic expression” in the beginning of this section, about the impact of Wi-Fi in our daily needs, in a broader context with historical and projected usage numbers.
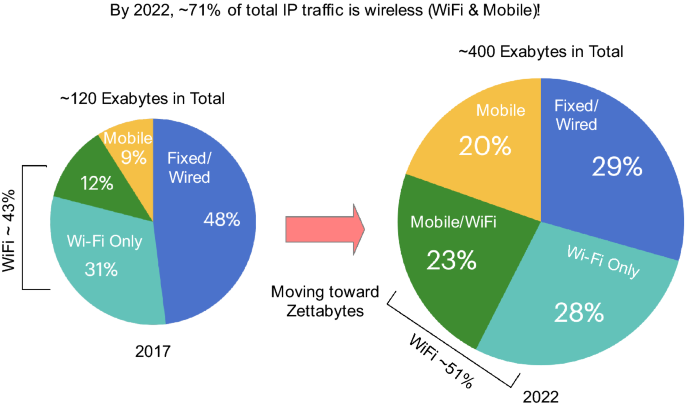
adapted from [5]
Approximate global monthly IP traffic for different Internet access methods in 2017 and 2022 (note Exabyte is 1018 bytes); Data
In this brief introduction we provided our view on the importance and impact of Wi-Fi technology. In the remainder of this paper we provide a holistic overview of the evolution of Wi-Fi technology and its applications. This is a huge area and it is very difficult to write a paper that includes every aspect of its history. As members of a pioneering research center in this field [6], we provide a historical perspective of evolution of Wi-Fi in the way that we experienced it in the past few decades (and the paper is driven by this personal lens). We approach this challenging task from three angles. First, how the physical (PHY) and medium access control (MAC) for wireless communications with Wi-Fi technology evolved and what were the novel wireless transmission technologies that were introduced in this endeavor. Second, how Wi-Fi positioning emerged as the most popular positioning technology in indoor and urban areas and how it has impacted our daily lives. Third, how other cyberspace applications, such as motion and gesture detection as well as authentication and security, are emerging to revolutionize human computer interfacing with the RF cloud of Wi-Fi devices.
2 Evolution of Wi-Fi Communications Technology
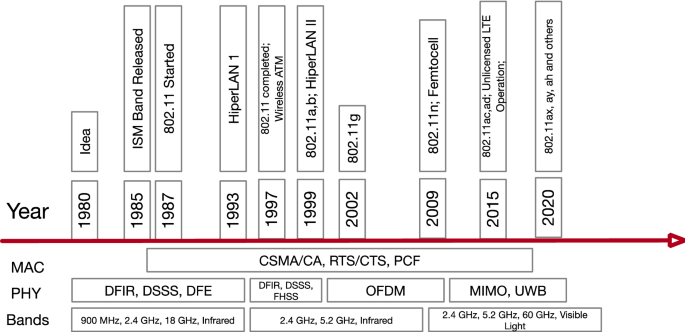
In this section we first discuss the origins of the PHY and MAC layer technologies for Wi-Fi by separating their origins into three eras: (i) prior to 1985, when the pioneering technologies for WLAN were invented, (ii) during the period 1985–1997, when IEEE 802.11 and Wi-Fi technology became IEEE standards and finally, (iii) from 1997 to the present, when orthogonal frequency division multiplexing (OFDM) and multiple-input multiple-output (MIMO) technologies enabled Wi-Fi to enhance the supported data rates from 2 Mbps to Gbps. Then we discuss the evolution of the market and the applications of Wi-Fi that eventually emerged.
2.1 The Origin of WLAN Technologies Before 1985
Around the year 1980, IBM‘s Rueschlikon Laboratory, Zurich, Switzerland began research and development on using InfraRed (IR) technology to design WLANs for manufacturing floors [7]. At that time, wired local area networks (LAN)s were popular in office areas and large manufacturers such as General Motors (GM) were considering their use in computerized manufacturing floors. To wire the inside of offices, it was necessary to snake wires in walls and was easier with low-height suspended ceilings. In manufacturing floors, there are limited numbers of partitioning walls and moreover ceilings are high and made of hard material. Consequently, WLAN technology offered itself as a practical alternative for manufacturing floors. Around the same time frame, HP Palo Alto Laboratory, California, reported a prototype WLAN using direct sequence spread spectrum (DSSS) with surface acoustic wave (SAW) devices (for implementation of a matched filter at the receiver) [8]. HP Laboratories at that time had open space offices without partitioning by walls, which again created challenges for wiring through the walls. Dropping wires from the ceiling to desktops was not aesthetically pleasing. It was in this time that optical wireless and spread spectrum, combined with spread spectrum technology emerged, that could support huge amounts of capacity for indoor WLANs to connect desktops and printers together in a local network [9, 10].
Prior to all this, Norm Abramson at University of Hawaii had designed the first experimental wireless data network, the ALOHA system [11]. The difference between the approach taken by IBM or HP and this approach was that ALOHA was an academic experimentation of wireless packet data networks with an antenna deployed outdoors with relatively low data rate modems at a speed of around 9600 bps. However, the concept had inspired low speed wireless data networking technologies such as Motorola’s ARDIS, and Ericsson’s Mobitex, (which we refer to as mobile data services now generally subsumed by cellular data services in 3G, 4G, and beyond). For WLAN technologies, the antenna is installed indoors, and the data rate needed to be at least 1 Mbps (at that time) to be considered by IEEE 802 standards organization community as a LAN [12]. The medium access control of both wireless data services was contention based, originally experimented in ALOHA, and later on evolving into carrier-sensing or listen before talk based contention access adopted by wired LANs by the IEEE 802.3 standard, commercially known as the Ethernet with some variation.
The main obstacle for commercial implementation of the early WLANs were interference and availability of a low cost wideband spectrum in which the WLAN could operate. Indoor optical WLANs did not need to consider regulation by the Federal Communications Commission (FCC) and they could potentially provide extremely wide bandwidths. However, optical communications cannot penetrate walls or other obstacles and thus, the operation becomes restricted to open areas, which are often small inside buildings. Spread spectrum was an anti-interference technology, which at that time could potentially manage the interference problem allowing multiple users to share a wideband spectrum [9, 10, 13]. In the summer of 1985, Mike Marcus, the chief engineer at FCC at that time, released the unlicensed Industrial, Scientific, and Medical (ISM) bands with restrictions of having to use spread spectrum technology for interference management [14]. For WLANs to become a commercial product, there was need for large bandwidths (at that time) and modem technologies that could overcome the challenges of indoor RF multipath propagation to achieve data rates beyond 1 Mbps required to be considered by the IEEE 802 committee as a LAN. The ISM bands and spread spectrum technology could address both issues.
2.2 Evolution of WLAN Technologies and Standards Between 1985 and 1997
The summer of 1985 was a turning point in the entrepreneurship for implementation in the WLAN industry. The FCC had released the ISM bands for commercial implementation of low power spread spectrum technology in May [14]. The suitability of RF spread spectrum and IR for implementing wireless office information networks had captured the cover page of the IEEE Communication Magazine in June [10]. Suddenly, several startup companies and a few groups in large companies, almost exclusively in North America, emerged to begin developing WLANs using spread spectrum and infrared technologies. Infrared devices did not need FCC regulations because they operate above the 300 GHz frequency, the highest governed by this agency. Among the exceptions for locations of these companies, was a small group in NCR, Netherlands, which designed the first Direct Sequence Spread Spectrum (DSSS) technology to achieve 2 Mbps [15, 16]. Other companies, such as Proxim, Mountain View, CA, resorted to Frequency Hopping Spread Spectrum (FHSS), and a third group led by Photonics, supported by Apple, resorted to an IR solution for WLANs. All three groups could achieve 2 Mbps. These three groups, originally started in the late 1980’s, laid the foundation for the first legacy IEEE 802.11 standards series, finalized in 1997. The final standard for DSSS and FHSS operated in the 2.4 GHz ISM bands. Other exceptions in technologies were efforts by Motorola, IL and WINDATA, Marlborough, MA. Motorola introduced a revolutionary WLAN technology operating in the 18 GHz licensed bands achieving 10 Mbps using a six sectored antenna configuration [17, 18], and WINDATA, achieved 6 Mbps in a dual band mode with 2.4 GHz for uplink and 5.2 GHz for downlink. The work presented in [17, 18] was the first time a wireless network was adopting frequencies in 18 GHz with directional antennas. We may refer to this work as the first attempt to use close to mmWave technology for modern wireless networking, which is now adopted by 5G cellular networks [19]. However, mmWaves cannot penetrate walls well, which restricts their coverage in indoor areas. This restriction is less of a concern in cellular networks with outdoor antenna deployments.
The first academic research in the physical layer of WLANs began at the Worcester Polytechnic Institute, Worcester, MA in Fall of 1985 [6]. The early academic research literature in this area began with the empirical modeling of the multipath radio propagation in indoor areas [20,21,22,23,24,25], examining decision feedback equalization (DFE) [26], and M-ary orthogonal coding [27] to achieve data rates beyond the 2 Mbps rates studied by the IEEE 802.11, to achieve rates on the orders of 20 Mbps, and the integration of voice and data for WLAN [28]. A form of M-ary orthogonal signaling was adopted by IEEE802.11b standard, DFE was adopted by the Pan European HIgh PERformance LAN (HIPERLAN)-I standard, and a form of OFDM was implemented in HIPERLAN-2 and IEEE 802.11a standards. A breakthrough, patented in this era, was the application of OFDM to WLANs, first filed by the Commonwealth Scientific and Industrial Research Organization (CSIRO), Sydney, Australia [29]. The origins of equalization, quadrature amplitude modulation (QAM), and OFDM transmission technologies were first implemented for commercial voice band communications [30]. The use of DFE was first adopted for wireless data communications over multipath troposcatter channels in military applications [31] and M-ary orthogonal coding was an extension to Code Division Multiple Access (CDMA) to increase the capacity for military applications [32]. The novelty of these technologies in this later time was in their application in commercial WLANs in non-wired and non-military applications.
The IEEE group for WLAN standardization was first formed as IEEE 802.4L in 1998. The IEEE 802.4 group was devoted to Token Bus LANs for manufacturing environments and was on the verge of disbanding. The rationale for introducing WLANs in this group was that new IEEE standards usually begin in a closely related standard and after going through the establishment procedure, may form their own group and standard series. The IEEE 802.11 group was the same group from IEEE 802.4L formed later in July 1990 [33]. In the early days of this standard the important challenge was to find the correct direction for the future technology among a number of acceptable technologies. In 1991, the standards group participated in the first IEEE sponsored conference to address this issue [34]. The early IEEE standards for wired LANs were differentiating from each other through their MAC method. IEEE 802.11 was the first with three MAC mechanisms (that could work together) and three PHY layer methods. The legacy IEEE 802.11 standard was completed in 1997 with three PHY layer recommendations, DSSS and FHSS operating in the 2.4 GHz ISM bands and Diffused Infrared (DFIR) wireless optical options. All three PHY layer options operated at raw data rate options of 1 and 2 Mbps and employed three possibilities for the MAC: carrier sensing - CSMA, request and clear to send - RTS-CTS, and polling (point-coordination-function) - PCF. RTS/CTS and PCF were designed to operate in conjunction with the base CSMA with collision avoidance (CSMA/CA).
The HIPERLAN was another WLAN standardization activity, sponsored by the European Telecommunications Standards Institute (ETSI), which began its work in 1992. The HIPERLAN-1 standard was the first attempt to achieve data rates above 10Mbps using DFE technology and in the 5 GHz unlicensed bands [35]. This standard was also completed in 1997, but it failed in developing a market for itself. Another more popular but extensive standardization activity for wireless indoor networking in this era was Wireless Asynchronous Transfer Mode (W-ATM), which aimed to integrate local wireless traffic with an ATM backbone wired technology [36, 37]. A comparison of this technology with Wi-Fi is available in [38].
In summary, it is fair to say that during the 1985–1997 era, the WLAN industry was in the process of discovering technologies for wideband indoor wireless communications and it examined spread spectrum, M-ary orthogonal coding, IR, licensed bands at 18 GHz with directional antennas, DFE, and OFDM technologies and the importance of the analysis of the effects of multipath and appropriate mitigation techniques to achieve higher data rates. The spread spectrum and Infrared technologies of the legacy IEEE 802.11 standard were the only technologies which survived in the market and a modified form of these technologies have remained in other popular standards such as Bluetooth, using FHSS and ZigBee using DSSS. M-ary orthogonal coding and OFDM appeared in later standards. This era also opened channels for dissemination of research and scholarship through publication channels. The first IEEE workshop on WLAN (1991), and the IEEE International Symposium on Personal, Indoor, and Mobile Communications (1992), hosted first panel discussions on the future of the WLAN industry in cooperation with the IEEE 802.11 standardization organization. The year 1994 marked the establishment of the first scientific journal, the International Journal of Wireless Information Networks, and the first scientific magazine related to this subject, IEEE Personal Communications, which later changed its name to IEEE Wireless Communications. The pioneering textbooks in Wireless Information Networks [39] and Wireless Communications [40] also emerged in this era.
2.3 Evolution of WLAN Technologies and Standards After 1997
The IEEE 802 standards define MAC and PHY specifications of local networks as standards for vendors to be able to interoperate. Figure 3 shows the evolution of the PHY and MAC layers of the IEEE 802.11 standards from the beginning to the present. The first step of evolution of the standard after completion of the legacy 802.11 standard in 1997, was the IEEE 802.11b standard that used complex M-Ary orthogonal coding known as Complementary Code Keying (CCK). The IEEE 802.11b standard was completed in 1999. Devices using this standard operated at speeds up to 11 Mbps with a fall back to 1–2 Mbps using the legacy 802.11 standard. Both IEEE 802.11b and the legacy IEEE 802.11 devices operated in the 2.4 GHz bands. In 1999, the IEEE standards body also completed specifications for IEEE 802.11a operating at 5.2 GHz using OFDM transmission technology to achieve data rates up to 54 Mbps. The IEEE 802.11a PHY layer was coordinated with the efforts in the HIPERLAN-2 standard in Europe [41]. In comparison with Wi-Fi, the centralized MAC of HIPERLAN-2 [42] was expected to allow better management of quality of service, vital to the cellular telephone industry. Perhaps that was the motivation of Ericsson to pursue the leadership of this effort. However, in a manner similar to wireless ATM, this standard did not achieve commercial success. This could be because in wide area networking we have large number of users with less bandwidth resources and rationing this scarce resource requires centralized supervision by enforcing quality of service rules. In local areas with abundant availability of bandwidth and only a few users, a distributed MAC would be more practical in that time frame. Although a new standard for integration of local and metropolitan area networks, such as HIPERLAN-2 or wireless ATM, did not became a reality, the need for this integration of cellular networks with Wi-Fi, became a reality. The concept of integration of Wi-Fi with cellular using vertical hand-offs and mobile IP technology emerged in the early days of commercial popularity of Wi-Fi [43] and it has prevailed all the way along up to the time of this writing but this time with operating system and software control. The continuation of the ideal of new standards for local operation continued into Femtocells [44] and long-term evolution-unlicensed (LTE-U) [45] – operation of 4G cellular networks in the unlicensed spectrum, but neither has created any serious challenge to the Wi-Fi market yet. In the same way that the WLAN industry in its early days of survival resorted to point-to-multipoint outdoor installation for wider area coverage, it can be thought that Wi-Max [46] emerged as a successful application of local area centralized medium access control technologies for outdoor antenna deployments. The wireless ATM, HIPERLAN, Femto-cell, LTE-U and Wi-MAX technologies created a significant hype in scientific publication venues and among national funding agencies, but they failed to keep investors in developing these technologies as happy as those that invested in Wi-Fi. Later, in 2003, the IEEE 802.11g working group defined OFDM operation in 2.4 GHz with the same data rates as IEEE 802.11a, which expanded the horizon for Wi-Fi market.
The breakthrough in wireless communications at the turn of the twenty first century was the discovery of multiple antennae streaming benefitting from space time coding (STC) and MIMO technology. The foundation of multiple antenna streaming is based on two technologies: adaptive antenna arrays to focus the beam pattern of antennas and space time coding (STC) which is a coding technique enabling separation of multiple streams of data with coding. The benefits of multiple transmitting and receiving antennas existed in the antenna and propagation society literature since the 1930’s [47]. Seminal work on STC [48,49,50] enabled multiple streams of data and that is why it is considered as one of the most important worldwide innovations around the turn of the twenty first century. Multiple streams of data using MIMO technology in conjunction with OFDM and benefitting from STC opened a new horizon in scaling the physical layer transmission rates in multipath fading channels [51]. The next giant step in the evolution of technology for the IEEE 802.11 community was the introduction of IEEE 802.11n in 2009, using MIMO technology to enable multiple data streams to achieve raw data rates up to 600 Mbps both in the 2.4 and 5.2 GHz bands. Other standards such as IEEE 802.11ac and 802.11ax, followed the same OFDM/MIMO technology.
Another major hype in physical layer technologies for wireless communications was mmWave pulse transmission technology. The IEEE 802.11ad group adopted mmWave pulse transmission technology in the 60 GHz band with utra-wideband (UWB) transmission bandwidth exceeding 2 GHz to achieve data rates on the order of Gbps. Although mmWave technology became an important part of the 5G cellular networking industry [19], IEEE 802.11ad and 802.11ay, as the first completed standards using these technologies have not been successful in attracting a huge share of the WLAN market. As we explained earlier, mmWaves in indoor areas has coverage restriction that does not apply to outdoor antenna deployments.
Regarding the MAC of the IEEE 802.11, the main two techniques which became dominant were CSMA/CA and request/clear to send - RTS/CLS. Carrier sensing with collision avoidance—CSMA/CA was a practical extension to the wireless medium of CSMA/CD (collision detection), which was adopted for the IEEE 802.3 standard, commercially known as Ethernet. The IEEE 802.11 devices grew with the name “wireless Ethernet” and CSMA/CA would enable Ethernet to finally have a wireless extension. The RTS/CTS mechanism was originally designed to address the hidden terminal problem, but it became more popular for application with directional antennas for IEEE 802.11ac, ad. An analytical comparison of these two MAC techniques is a challenging problem that received a very thorough and popular analysis in the year 2000 [52].
A good survey of all these standards is presented at Wikipedia [53]. Here, we argue that all major PHY layer technologies evolved for wireless information networks: optical wireless, spread spectrum, M-ary orthogonal coding, OFDM, MIMO, and mmWave technologies were first adopted by the IEEE 802.11 standardization community. Then, DSSS and orthogonal signaling in 2G/3G, OFDM/MIMO in 4G, and mmWave in 5G/6G cellular telephone technologies, came after the adoption of these technologies in IEEE802.11 standards. The MAC of cellular telephone industry is centralized and different from that of WLANs, primarily to accommodate high traffic densities and support higher level of mobility for users with metropolitain area coverage. The IEEE 802.15 wireless personal area networks followed a similar pattern by adoption of FHSS for Bluetooth and DSSS for ZigBee, after they were first introduced by the IEEE 802.11 standard. The MAC of Bluetooth and in particular ZigBee carry similarities with those of the MAC of IEEE 802.11. Therefore, it is fair to say that the WLAN industry pioneered the design of the dominant PHY technologies of today’s wireless networking industry and this is a huge technological impact in the communication of humans, devices, and machines.
2.4 Evolution of Wi-Fi Applications and Market
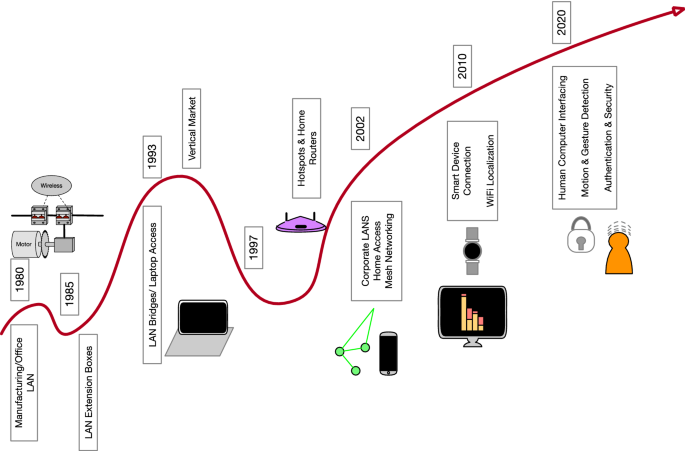
Applications fuel the market, and they are intimately linked to the network through devices running these applications. Local area networks were networking computers to share common peripheral devices such as printers or storage memories and later machines in a manufacturing floor. In the late 1980’s and early 1990’s, when the WLAN industry began to test the market, Personal Computers (PC) and Workstations were competing to capture the market of mini-computers. Laptops became popular in this market a little later. From the networking point of view in that era, engineers were searching for wiring solutions for the growing market of these devices to connect them with minimal effort. The early WLAN startups were thinking of wireless as a replacement to wired LANs to connect PC’s in open areas such as manufacturing floors or open offices without partitions. These companies were assuming that these small computers will grow on office desks or on manufacturing areas in clusters. The idea was that if we connect this cluster of desktop computers to a hub and then we connect the hub to a central node connected to the Ethernet backbone, we will avoid snaking of wires or wires hanging from the ceilings of manufacturing floors and offices. In a typical startup proposal for venture capital, these companies were arguing that close to half of the cost of the LAN industry was associated with installation and maintenance of these networks, which can be vanishingly small when we use wireless technology. As a result, the first WLAN products were shoe box sized hubs and central units and following the above argument, these companies were estimating that a market of a few billion-dollars would emerge for these devices in early 1990’s. Based on this idea a typical startup company or a small group in a large company could raise up to $20 M at that time, adequate to support a design and marketing team to get the product going. Therefore, the early products from NCR, Proxim, Aironet, WINDATA, Motorola, NCR, Persoft, Photnics and others appeared in the market (see Fig. 4a for samples of these products). The reader can find a variety of photos of these historical WLAN products in the proceedings of the first IEEE Workshop on WLAN [34]. This workshop was held in Worcester, MA, in parallel to the IEEE 802.11 official meeting to decide on the future of this industry. Around the year 1993 these products were in the market but the expected few billion-dollar market developed only to a few hundred million dollars. These sales were mostly for selected vertical applications and by research laboratories discovering the technology, not for the horizontal market for connecting desktop computers everywhere. This resulted in a retreat in the original few tens of companies, searching for a new market domain.
During the market crash of 1993 for the WLAN industry designed for connecting clusters of desktop computers, two new applications emerged. The first solution was point-to-point or point-to-multipoint WLAN bridges. The idea was to allow WLANs to operate outdoors and add a strong roof top antenna to take advantage of free space propagation and antenna gains to extend the expected 100 m indoor coverage to outdoor coverage spanning a few miles. As examples of these markets, two hospitals in Worcester, MA, which were a few miles away could connect their networks with low cost private WLANs, instead of using expensive leased lines from telephone companies. Or, Worcester Polytechnic Institute could connect the dormitories to the local area network of the main campus. The other idea was to design smaller wireless PC Cards for the emerging laptop market. Figure 4b shows the picture of the Roamabout access point box and the laptop wireless PC Cards of the first successful product of that type, designed at Digital Equipment Corporation, Maynard, MA. These devices were the showcase of the second IEEE Workshop on WLANs, October 1996 [54]. Examples of a practical market for laptop operation included large financing corporations such as Fidelity in Boston, who would purchase laptops for their marketing, sales, and other staff. Such companies wanted their staff to be connected to the corporate network, when in office.
The next wave of market demand for WLANs was for small office/ home office (SOHO) application, which began around 2000. The authors believe that this story began in the mid-1990 with the penetration of the Internet to homes with service providers like America online (AOL) for small indoor area distribution of signals. The penetration of the Internet in homes fueled the development of cable modems and digital subscriber line (DSL) modems for high data rate home services and with that came the growth in the number of home devices and demand for Home-LAN technology. Several ideas such as using home wiring or electricity wiring for implementation of Home-LANs were studied, but Wi-Fi emerged as the natural solution. At that time, the price of a Wi-Fi access point (AP), such as the one made by Linksys, had fallen to below $100 and wireless PC Cards could be purchased with a reasonable price of a few tens of dollars. The original early shoe boxes had been selling for a few hundred dollars for the hub and up to a few thousand dollars for the AP! With these lower prices, coffeeshops and other small businesses could afford to provide free Wi-Fi and homeowners could bring Wi-Fi home. This was perhaps the first large market bringing Wi-Fi from office to the home. During the 2000’s despite the crash of the .com industry, the Wi-Fi market in this domain began to grow exponentially. The exponential growth of Wi-Fi for SOHO encouraged consumer product manufacturing to consider Wi-Fi for integration in their products (e.g., in digital cameras and TV monitors). This market was however not that large, and the ease of Wi-Fi networking did not exist. The integration of Wi-Fi in the iPhone was the next major marketing break-through for Wi-Fi popularity and market growth. Integration of Wi-Fi into smartphone increased the sale of Wi-Fi chipsets to billions and further enabled Wi-Fi based positioning. More recently Wi-Fi applications expanded by emergence of motion and gesture detection as well as authentication and security with Wi-Fi signals to facilitate human computer interaction. Figure 5 summarizes the evolution of Wi-Fi applications. We provide an overview of these cyberspace application using the Wi-Fi signal in the remainder of this paper.
3 From Wi-Fi to Wi-Fi Positioning – Emergence of Another “Killer App”
In the early 1990’s, when the expected market for WLANs did not emerge, those invested in this emerging technology began to discover reasons for the lack of success. These were the CEO’s of startups and managers of the WLAN projects in larger companies. Some were associating the lack of success to the delay in finalizing the IEEE 802.11 standard and some to the lack of a “Killer App”. The standard itself was completed in 1997 (with interoperability tests) and soon, deployment in SOHO scenarios appeared as the “Killer App” in the late 1990’s. Adoption of Wi-Fi in smart phones in the late 2000 s was another breakthrough “Killer App” of Wi-Fi technology, which enabled these devices to execute a number of user applications such as integration of search engines, email, and large file transfers using smart phones. Other networked applications that were typically done on a desktop using the Internet followed (e.g., e-commerce and banking). However, the Wi-Fi Positioning engine was perhaps the most innovative “Killer App” related to Wi-Fi technology that was introduced by the iPhone. When Steve Jobs introduced Skyhook of Boston’s Wi-Fi positioning technology in the iPhone, and he called it “Cool” and a “neat idea” [55], because it was different.
3.1 The Origin of Wi-Fi Positioning
Because of the commercial success of the Global Positioning System (GPS) in the mid-1990’s, the fact that GPS does not work properly in indoor areas, and the FCC mandate on E911 services for cellular networks, the indoor geolocation science and technology began to emerge in the late 1990’s [56, 57]. The expensive cost of dense infrastructure needed for commercial positioning applications led that industry to resort to opportunistic positioning. Opportunistic Wi-Fi positioning using received Wi-Fi signals radiated from the Wi-Fi access points, originally deployed for wireless communications in office areas, was the first idea to attract attention for a cost effective indoor geolocation system [58, 59]. The received signal strength (RSS) or time of arrival (TOA) of the signals radiated from the access points could be used for positioning since the locations of the access points were known and could be used for this purpose. The RSS was a quantity that was easier to measure but it was not accurate enough for good location granularity. The use of RSS for positioning became practical only by incorporating intelligence through training the system with fingerprinting and using pattern recognition algorithms to find the location [60, 61]. This training was done with similar devices that collected data at known locations to make up the training fingerprints. The more accurate TOA measurements [59] needed additional design to be incorporated through a TOA acquisition system. The widespread deployment of Wi-Fi in office areas was more fertile for commercial development and a few companies, such as Ekahau, Helsinki, Finland, adopted that technology as their Wi-Fi positioning indoor geolocation system. Today this Wi-Fi positioning industry is sometime referred to as “real time positioning system” RTLS) [62]. The commercial success of RTLS was rather limited and it never generated a substantial market for Wi-Fi positioning.
Another approach to Wi-Fi positioning was to collect the fingerprint of locations from the APs from a vehicle driving in the streets and tagging the fingerprints with the GPS location reports of the vehicle at the time of measurement. This was the approach used by Skyhook Wireless, Boston, MA, which was adopted by the iPhone and was trademarked as “Wi-Fi Positioning System” (WPS) by Skyhook [62]. The difference between RTLS and WPS are: (1) RTLS typically covers only one building while WPS covers a metropolitan area, (2) fingerprinting in RTLS for a given area of coverage is much more expensive than WPS, (3) RTLS provides an accuracy of around a few meters while WPS provides for accuracies on the order of 10-15 m. Larger coverage areas with accuracies of 10-15 m enabled turn-by-turn direction finding for vehicles in the metropolitan areas that was the highlight of positioning applications in the original iPhone [55]. As a result, WPS became a commercial success and a highlight of the magic of iPhone applications. Today, Skyhook’s database contains over a billion AP locations worldwide and its database receives over a billion hits per day from smart device applications using WPS technologies. Google, Apple and other cyberspace giants have formed their own WPS system with their own database of APs along with that of the Skyhook.
3.2 Emergence of Location Intelligence from WPS
WPS is a device-based positioning system, i.e., a device reads the RSS of surrounding Wi-Fi devices with their MAC addresses. These readings are transferred to a central server with a database of the mapping of fingerprints to position and the system can determine the location of the device using the fingerprint database. Thus, communication link to carry these information between the device and the server is essential here, which Wi-Fi already provides. This process traditionally takes place in two steps, fingerprinting and positioning. During the fingerprinting phase, a data acquisition device located in a vehicle drives on the streets. In this phase the MAC addresses of the APs and their associated RSS are sampled approximately every second and each sample is tagged with the GPS reading of the location at the time of sampling. The fingerprint in the database, the MAC addresses and the GPS readings are post processed with proprietary algorithms to associate the MAC addresses of each AP to a location based on GPS readings. In this way, the WPS system builds a database of locations of the APs in the areas that the vehicles drive through. When a device, not knowing its location, sends the MAC address of an AP and RSS readings to the server, the server uses another proprietary algorithm to position the device and determine its location. The major WPS service providers, Skyhook, Google, and Apple, each receive approximately one billion requests per day from millions of devices. The one billion hits each associate a personal device address to a location and one can track the movements of the device. Applications drawing from this motion tracking capability of WPS are referred to as “location intelligent” and are said to be providing location-based services. One simple location intelligence application is the location-time traffic analysis. We may grade the density of hits per-hour of the day to determine where the people are going, and smart marketing strategies can benefit from that data. Other location intelligent applications include “geofencing” of elderly people, animals, prisoners, suspicious people, real world consumer behavior, location certification for security, positioning IP addresses, and customizing contents and experiences. During the recent COVID pandemic, Apple made its mobility data (when people were asking directions – and thus location information) public to enable assessing the social distancing and quarantine postures in various cities and communities [63]. Of course, this data also includes cell phone technology, but it is an indication of how far sensing signals from mobile devices has come, starting with Wi-Fi positioning.
The future directions in Wi-Fi positioning is in the integration of RSS signals with other sensor readings on smart devices (accelerometers for instance) to enhance the precision and flexibility of positioning. There are research works on integration of mechanical sensors such as accelerometer and gyroscope on robotic platforms with Wi-Fi positioning [64], there are works in integrating more precise UWB positioning with limited coverage with wider coverage Wi-Fi positioning [65], and frameworks for generalizing fingerprinting in multi-sensor environment [66, 67]. Other researchers investigate submeter Wi-Fi positioning using Wi-Fi channel state information (CSI) [68].
4 Wi-Fi and Emerging Cyberspace Applications
Wi-Fi localization, either for local indoor areas (what we referred to above as RTLS) or for metropolitan areas (which we referred to as WPS) makes use of the RSS feature from APs that are broadcasting signals, by reading their broadcast quasi-periodic beacon signal. Beacons are used to advertise the availability of an AP thereby enabling other devices like smartphones or laptops to access the Wi-Fi network (called basic or extended service area in the standard). A device that reads the beacon only for localization does not need to connect to the AP because it only needs the MAC address and the RSS information for positioning itself. Access Points radiate a radio frequency (RF) cloud around themselves which are available to any device in their area of coverage. The RSS is one feature of the Wi-Fi RF cloud, which can be measured easily without any coordination between the transmitter and the receiver. With some coordination, the receiver can measure the Time of Arrival (TOA) of a signal as well. Today, the dominant transmission technique in Wi-Fi is MIMO-OFDM. Devices which can use MIMO_OFDM can also measure Direction of Arrival (DOA), channel impulse response (CIR), and the Channel State Information (CSI) of the multipath medium between the transmitter and the received [69]. These features (as well as the RSS feature) vary statistically depending on the multipath characteristics arising from the motion in the environment. Consequently, it is possible to use these features for motion and gesture detection. In this section, we begin by describing these statistical behaviors and following that we briefly review the emerging research benefitting from analyzing these statistical changes in features, toward the design of cyberspace applications for human-computer interactions.
4.1 Characteristics of Features of Wi-Fi Signals in Multipath
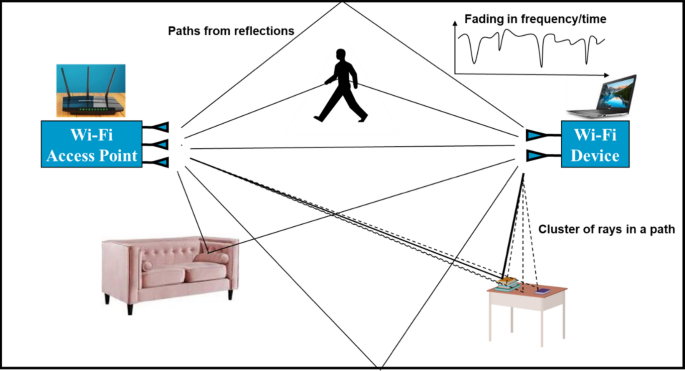
Figure 6, illustrates a general line-of-sight (LOS) scenario for a MIMO-OFDM Wi-Fi communication with typical multipath propagation. Multiple paths are reflected from walls and other stationary and moving objects in the environment. These paths are often clustered due to scattering from smaller objects located close to each other. In an ideal situation, the stationary baseband CIR for wireless devices operating in multipath indoor areas is represented by:
where \((\alpha_{i} ;\tau_{i} ;\theta_{i} ;\psi_{i} )\,\) are the magnitude, TOA, phase, and DOA of the i-th path, and N is the number of multipath components. In this equation the phase of the arriving path and the TOA are related by \(\theta_{i} = 2\pi f_{c} \tau_{i} \,\). Therefore, if we measure the TOA, we can calculate phase and vice versa. Since the phase is a periodic function, in calculation of the TOA from the phase we should consider such ambiguities [57]. The TOA, amplitude, and phase of each path as well as the RSS can be calculated from the length of the path, by:
, where \(f_{c} \,\) is the carrier frequency of the signal, \(\lambda = c/f_{c} \,\) is the wavelength of the signal, \(d_{i}\), is the length of the path, and c is the speed of light. If we have an antenna array, we can calculate the DOA from TOA differences between the received signals from different array elements. When we have motion in the environment, either by moving the location of the devices or objects move in the environment, the lengths of the various paths change affecting features such as RSS, TOA, and DOA. In addition, due to Doppler shift effects, a change in the length of a path with the velocity of \(v_{i} \,\) meters per second causes a frequency off-set in the carrier frequency calculated from [57] :
In summary, if a receiver can measure the CIR and the frequency off-set, it can monitor the length and direction of the path as well as the velocity of changes in the path lengths.
As shown in Eq. (2), the amplitude of the received signal, \(\alpha_{i}\), from a path changes inversely with the increase in the path length, \(d_{i}\). The phase of the arriving signal from a path, \(\theta_{i}\), changes rapidly for a value of \(2\pi\) each time the length of the path increases by a value equivalent to the wavelength of the signal, \(\lambda\) . The rapid change in phase of the arriving paths causes fading and these rapid changes are caused by motion of the device, motion of people around the devices, and by the changes in frequency of operation. In the wireless communication literature, fading characteristics is studied under temporal, frequency-selective, and spatial fading [39].
The traditional application of measurements of the CIR is in high-speed wireless communications and in radars. Modern applications that use CIR measurements are in wireless positioning, gesture, and motion detection, and in authentication and security. Each application relies on certain specific features of the CIR and for that needs to measure those features with certain precision at the receiver. The accuracy of measurement of these features at a receiver relies on training (known signals), the bandwidth of the system, availability of antenna arrays at the receiver, and accuracy of synchronization between the transmitter and the receiver. As a result, the specific implementation of these applications have unique challenges and demand research and development and decades of years of evolution. Traditional radar and digital communication systems were built around the second World War and today we are still developing new cyberspace applications around them. What is changing is the application environment and characteristics of multipath inside those environments. As we move from open areas to sub-urban, densely populated urban areas, and indoor areas, the multipath propagation of RF signals increases, and design of applications faces new challenges.
The measurement of multipath characteristics of the channel was a very challenging problem in the early 1970’s [70]. Wideband digital communication systems evolving in this era needed the estimate of multipath arrivals to enhance their data rates. Wideband multipath channel measurement in that period would be a subject for a Ph.D. thesis [71]. Today, all wireless communication devices measure the multipath characteristics as a routine in the design of their systems.
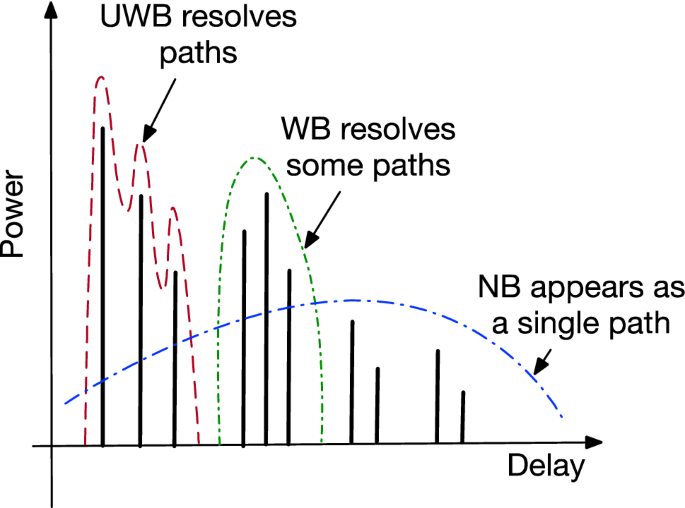
If the bandwidth of the system is wide enough so that the width of the transmitted communication symbols, the inverse of the bandwidth, is less than the inter-arrival time of the paths, a sensitive enough receiver can isolate each path and measure the features precisely. If the bandwidth of the channel is not wide enough, a receiver can only detect a cluster of paths as one path. In wireless communications we can categorize device receivers into three categories, ultra-wideband (UWB),Footnote 3 wideband (WB), and narrowband (NB). UWB systems are capable of measuring most individual paths, WB receivers measure multipath arrivals but each path is in reality an aggregate of a cluster of paths, and NB receivers receive the signal from many paths as essentially a single path that combines all multipath arrivals (see Fig. 7). When a receiver detects a path that is indeed the combination of several neighboring paths, due to fast variations of the phases of the original path, the amplitude of the detected path experiences Rayleigh or Rician fading and the TOA of the detected path obviously is something very different from any of the individual paths in wireless communication applications, fading causes huge degradation of the maximum achievable data rate, and to compensate for that the research community have discovered equalization, spread spectrum, OFDM, and MIMO technologies in the past several decades [39]. The popular TOA-based location related applications measure the distance from the delay of the TOA of the direct path between the transmitters and the receiver and integration of multiple paths in a single path at the receiver causes huge errors in distance estimation (1 m error for every 3 ns error in delay).
The receivers of wireless communication devices employing these technologies measure the characteristic of the communication channel and characteristics of these measurements vary, depending on the architecture and bandwidth of the system. Empirical measurements and modeling of multipath RF propagation in indoor areas in the late 1980’s, first showed that if the bandwidth exceeded 100 MHz the amplitude of multipath arrivals follows a lognormal distribution, caused by shadowing, and they do not follow the commonly assumed Rayleigh or Rician multipath fading characteristics [24]. Therefore, we may consider Wi-Fi technologies using bandwidths on that order as UWB systems that can resolve the paths. The characteristics of CIR measurements with UWB systems is that the amplitude of the paths follow a lognormal distribution that is much more stable than Rayleigh/Rician distributions, and the TOA measurements are precise for calculation of the delay of the paths. The IEEE 802.11ad devices certainly follow the UWB characteristics. The IEEE 802.11ac options with bandwidth up to 160 MHz gets close to observing UWB features. However, legacy IEEE 802.11 and the popular 802.11 a,g,n,ac,ax,af can be considered as WB systems with bandwidths of approximately 20-40 MHz (and sometimes up to 80 MHz). The IEEE 802.11 standards using OFDM have sub-carriers with a bandwidth of approximately 20 MHz/64 = 375 kHz per carrier, which is considered NB. In summary, channel measurements for NB transmissions provide for a stream of Rayleigh fading amplitudes and uniformly distributed phases. The phase measurements do not support a reliable measure of distance and WB systems provide multiple streams of NB data. The UWB systems provide for multiple streams of slow lognormally fading signals with multiple streams of phases that are beneficial for accurate measurements of the delays of the associated paths.
The most popular Wi-Fi devices at the time of this writing, IEEE802.11n and IEEE 802.11ac, use MIMO-OFDM technology with three transmitters and two receiver antennas, shown in Fig. 6. The OFDM signal has 64 sub-carriers, using 52 of these carriers for communication data. In addition, to the magnitude and phase of the carriers they also provide the frequency off-set from the center frequency as well as six streams of magnitude and phases of the CSI data. Depending on the quality of the beam forming algorithm to sharpen the beam, the CSI data can represent a single path or a cluster of paths arriving from a direction. If it is a cluster, the amplitude samples have a Rayleigh distribution and if it is a single path the amplitudes should be more stable with a lognormal fading behavior. The number of paths in the cluster also governs the accuracy of delay of the path measurement using the phase of the received CSI stream [72]. Recently, these data streams have been paired with artificial intelligence (AI) algorithms to initiate research in several cyberspace applications.
4.2 Emerging Cyberspace Applications of Wi-Fi
In recent years, researchers have studied a variety of Wi-Fi “RF cloud” features in several cyberspace applications and for the enhancement of local area positioning systems. The idea of using the preamble of OFDM signals, first introduced in HIPERLAN-2/IEEE 802.11a standard, for TOA localization was discussed at the emergence of this standard in [59]. In this work, the pseudo noise (PN) sequence used in the preamble of the OFDM signal is used for TOA positioning. Like the measurement of timing in GPS, the TOA is measured from the time displacements in the sharp peak of the autocorrelation function of the PN-sequence. It is also possible to measure the TOA from the phase of the received signal; however, this is very sensitive to multipath fading [57]. OFDM/MIMO systems reduce the multipath allowing a more accurate measurement of TOA using the phase of the received signal. Recently, the measurement of TOA using the phase of Wi-Fi signals with OFDM/MIMO was used for fine-grained micro-robot tracking in [68, 73]. The experience in that work suggests that in a line-of-sight (LOS) situation (close distance between transmitter and receiver), where the multipath features are not significant, the phase of the received signal provides a reasonable estimate of the distance. Others have experimented with CSI fingerprints to enhance indoor Wi-Fi positioning [74]. As we explained in Sect. 4.1, CSI provides multiple streams of magnitude and phase and the phase information can be used for TOA estimations. The research trend in [59, 68, 73, 74] opens a horizon for higher precision Wi-Fi positioning, as they are compared to RSS based Wi-Fi positioning in local indoor [58, 75], and wider metropolitan areas [62, 76, 77].
In the past decade, the design of novel “cyberspace intelligence” applications that opportunistically benefit from the “RF cloud” radiated from signals used for wireless communications and short range radars, has been a fertile area of research [69]. These applications take advantage of statistical variations of RF signals propagated from the wireless devices, caused by motion in the environment to design applications that can detect gestures and motion or those used for authentication and security. Because of the widespread deployment and reach of Wi-Fi access points and the availability of Wi-Fi chip sets in almost every personal electronic device, as described in Sects. 2.4 and 2.5, a large body of this literature has evolved around this Wi-Fi RF cloud. Once again, the simplest feature of the Wi-Fi RF cloud is the RSS. Motions in the environment cause multipath fading resulting in changes in the RSS and statistics of this fading behavior as it relates to the speed of motion. The applications benefit from this behavioral change in the RSS to develop simple possibilities in detecting motion related human activity. This trend of research began in the early 2010’s and has evolved throughout that decade. As an example, the time- and frequency-domain multipath fading characteristics of the RSS from body mounted health monitoring sensors was examined in the lead author’s laboratory in the early 2010’s to differentiate among standing, walking, and jogging activities by humans [78]. In the mid-2010’s, when the infusion of AI to applications became popular, the same idea with more complex activity classifications with AI algorithms was pursued [79]. In the middle of these activities, hand motion classification using RSS and the frequency offset of OFDM signals from Wi-Fi devices when motion occurs between two devices without any body mounted device was reported to differentiate nine hand gestures [80]. Research in that direction encouraged the consideration of a more advanced feature such as the CSI for similar applications and suddenly a large body of literature emerged for a variety of related applications for human computer interaction that made extensive use of the statistical behavior of CSI from Wi-Fi signals. Approximately 150 of these papers are classified in [81]. These papers use CSI toward what is called as “device-free” human activity detection [82] all the way up to micro-gesture detection applications such as detecting hand motion while typing [83, 84].
In gesture and motion detection using RF signals, the work takes advantage of the effects of motion on changing the multipath propagation of signals and the resulting change in statistical behavior of the features of RF cloud to classify human activity. Similarly, it is possible to use the uniqueness of these variations for individual human motions to identify a person. For example, when we train a computer to detect the keystroke of a person using the CSI from Wi-Fi signals, the same system can identify that person as the keystrokes of one individual vary from that of another. This way, using the CSI for keystroke detection can also be used for human authentication for security purposes [83]. In recent years, a body of literature has also evolved for applications of the Wi-Fi RF cloud in authentication and security. Again, the simplest feature that is used is the RSS and it is possible to use the RSS behavior of body mounted sensors to identify a person [85]. Fundamentally, authentication is a binary decision-making process (is it Alice or not?) and activity classification is a multiple classification problem (is Alice jogging, walking, standing, or sitting?). In authentication we compare RF feature characteristics of one person to others, while in activity classification we usually compare different activities of a single person. Such similarities have led to the emergence of literature in using more complex CSI from Wi-Fi signals for device-free authentication such as those in [86]. Another survey of these categories of applications is available in [87].
The problem of entity authentication is for security – whether an authorized individual is performing an action. However, there is another branch of security application, concerned with generation of unique (and random so that it cannot be guessed) keys for encryption of the data communication between wireless devices sharing this natural broadcasting medium. The fundamental idea comes from the fact that the wireless communication channel between two devices is reciprocal [88, 89]. Therefore, when we measure the features of the communication channel between two devices, these features should be the same. However, the details of the electronic implementation of a device is unique to itself and that results in measurements which are not identical. If we can model these differences by a measurement noise, then we can quantize the measured feature based on the measurement noise to establish the same key at two ends of a wireless communication link. A survey of these physical layer security systems is available in [90, 91]. Geo-fencing, to ensure that Wi-Fi signal propagation can be confined to the inside of a building is another interesting application of radio propagation for information security [92].
Although in past decade these cyberspace applications of Wi-Fi signals have attracted significant intellectual attention for research, the commercial market is still waiting for a “Killer App” like Wi-Fi positioning and tracking. The industry is waiting for the next popular application of Wi-Fi signals to enhance cyberspace intelligence further.
5 Conclusions
In this paper we presented a historical perspective of the evolution of Wi-Fi technology in the way that the principal author experienced it (and subsequently the second author) since the inception of this industry in early 1980’s. The paper was prepared as a part of a special issue on the 25 anniversaries of the International Journal of Wireless Information Networks, which was established in 1994 as the first journal fully devoted to wireless networks. In the paper, we began by describing how Wi-Fi has impacted our daily lives and why it is playing this important role. Then we discussed how the dominant physical layer wireless communication technologies, wireless optical, spread spectrum, OFDM and MIMO, and mmWave UWB technologies, were first implemented in the IEEE 802.11 standards for Wi-Fi and how indoor radio propagation studies were conducted to enable these technologies. The rest of the paper illustrated how the RF cloud propagated from Wi-Fi devices enabled important cyberspace applications. We began this part by describing how Wi-Fi positioning revolutionized indoor geolocation science and technology. Then we explained how the RF cloud of Wi-Fi devices has enabled diverse cyberspace applications such as motion and gesture detection as well as authentication and security to hopefully lead the way to another revolution in human computer interfacing.
Notes
A version of this paper was originally presented as a keynote speech entitled “Evolution of Wi-Fi Access and Localization – A Historical Perspective”, IEEE VTC, Boston, MA, May 6, 2015. Material presented further evolved in other keynote speeches, the last one in Cybercon’19, Beijing, China, December 16, 2019.
In the recent pandemic, parents and children are using Wi-Fi for work and school, and its untethered feature has made a big difference to the way people have coped with social distancing and quarantines.
We use the term UWB differently here than before, where extremely narrow pulses of bandwidth on the order of a GHz are used for fine grained localization. The term UWB is also now used by commercial 5G systems differently.
References
K. K. K. Fong and S. K. S. Wong, Wi-Fi Adoption and Security in Hong Kong, Asian Social Science, Vol. 12, No. 6, pp. 1–22, 2016.
Pace Technical: “Is Fast Wi-Fi the Most Basic of Human Needs?” https://www.pacetechnical.com/fast-wifi-basic-human-needs/.
Berk-Tek, A NEXANS Company. “Basic Human Needs: Food, shelter, and…Wireless??” Aug 15th, 2017 https://eipblog.net/2017/08/15/basic-human-needs-food-shelter-andwireless/.
S. McLeod, Maslow’s hierarchy of needs, Simply Psychology, Vol. 1, pp. 1–8, 2007.
G. M. D. T. Forecast, Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2017–2022, Update, Vol. 2017, p. 2022, 2019.
V. Bahl, wireless research centers: building the future with wireless technology, ACM SIGMOBILE Mob. Comput. Commun. Rev., Vol. 4, No. 2, p. 37, 2000.
F. R. Gfeller and U. Bapst, Wireless in-house data communication via diffuse infrared radiation, Proceedings of the IEEE, Vol. 67, No. 11, pp. 1474–1486, 1979.
P. Freret, R. Eschenbach, D. Crawford and P. Braisted, Applications of spread-spectrum radio to wireless terminal communications, Proceedings of the IEEE NTC, Vol. 4, pp. 244–248, 1980.
Pahlavan, K., 1984, January. A review of wireless in-house data communication systems. In Proceedings Computer Networking Symposium (pp. 129-130). IEEE Computer Society.
K. Pahlavan, Wireless communications for office information networks, IEEE Communications Magazine, Vol. 23, No. 6, pp. 19–27, 1985.
Abramson, N., 1970, November. THE ALOHA SYSTEM: another alternative for computer communications. In Proceedings of the November 17-19, 1970, fall joint computer conference (pp. 281-285).
K. Pahlavan and A. H. Levesque, Wireless data communications, Proceedings of the IEEE, Vol. 82, No. 9, pp. 1398–1430, 1994.
K. Pahlavan, Wireless intra-office networks, ACM Transactions on Information Systems (TOIS), Vol. 6, No. 3, pp. 277–302, 1988.
Marcus, M.J., 1985, December. Recent US regulatory decisions on civil uses of spread spectrum. In IEEE GLOBECOM (Vol. 16, pp. 1-16).
Tuch, B.J., 1991, May. An ISM Band Local Area Network: WaveLAN. In IEEE Workshop on Local Area Networks, Worcester Polytechnic Institute, Worcester Massachusetts (pp. 103-111).
B. Tuch, Development of WaveLAN®, an ISM band wireless LAN, AT&T Technical Journal, Vol. 72, No. 4, pp. 27–37, 1993.
Freeburg, T.A., 1991. A New Technology for High Speed Wireless Local Area Networks, In IEEE Workshop on Local Area Networks, Worcester Polytechnic Institute, Worcester Massachusetts (pp. 127-139).
T. A. Freeburg, Enabling technologies for wireless in-building network communications-four technical challenges, four solutions, IEEE Communications Magazine, Vol. 29, No. 4, pp. 58–64, 1991.
T. S. Rappaport, S. Sun, R. Mayzus, H. Zhao, Y. Azar, K. Wang, G. N. Wong, J. K. Schulz, M. Samimi and F. Gutierrez, Millimeter wave mobile communications for 5G cellular: It will work!, IEEE access, Vol. 1, pp. 335–349, 2013.
K. Pahlavan, R. Ganesh and T. Hotaling, Multipath propagation measurements on manufacturing floors at 910 MHz, Electronics Letters, Vol. 25, No. 3, pp. 225–227, 1989.
S. J. Howard and K. Pahlavan, Measurement and analysis of the indoor radio channel in the frequency domain, IEEE Transactions on Instrumentation and Measurement, Vol. 39, No. 5, pp. 751–755, 1990.
S. J. Howard and K. Pahlavan, Doppler spread measurements of indoor radio channel, Electronics Letters, Vol. 26, No. 2, pp. 107–109, 1990.
R. Ganesh and K. Pahlavan, On arrival of paths in fading multipath indoor radio channels, Electronics Letters, Vol. 25, No. 12, pp. 763–765, 1989.
R. Ganesh and K. Pahlavan, Statistical modelling and computer simulation of indoor radio channel, IEE Proceedings I (Communications, Speech and Vision), Vol. 138, No. 3, pp. 153–161, 1991.
S. J. Howard and K. Pahlavan, Autoregressive modeling of wide-band indoor radio propagation, IEEE Transactions on Communications, Vol. 40, No. 9, pp. 1540–1552, 1992.
T. A. Sexton and K. Pahlavan, Channel modeling and adaptive equalization of indoor radio channels, IEEE Journal on Selected Areas in Communications, Vol. 7, No. 1, pp. 114–121, 1989.
K. Pahlavan and M. Chase, Spread-spectrum multiple-access performance of orthogonal codes for indoor radio communications, IEEE Transactions on Communications, Vol. 38, No. 5, pp. 574–577, 1990.
K. Zhang and K. Pahlavan, An integrated voice/data system for mobile indoor radio networks, IEEE transactions on Vehicular Technology, Vol. 39, No. 1, pp. 75–82, 1990.
O’sullivan, J.D., Daniels, G.R., Percival, T.M., Ostry, D.I. and Deane, J.F., Commonwealth Scientific and Industrial Research Organization (CSIRO), 1996. Wireless LAN. U.S. Patent 5,487,069.
K. Pahlavan and J. L. Holsinger, Voice-band data communication modems-a historical review: 1919-1988, IEEE Communications Magazine, Vol. 26, No. 1, pp. 16–27, 1988.
P. Monsen, Theoretical and measured performance of a DFE modem on a fading multipath channel, IEEE Transactions on Communications, Vol. 25, No. 10, pp. 1144–1153, 1977.
P. E. R. K. Enge and D. I. L. I. P. V. Sarwate, Spread-spectrum multiple-access performance of orthogonal codes: Linear receivers, IEEE Transactions on Communications, Vol. 35, No. 12, pp. 1309–1319, 1987.
Hayes V., 1991, May.Wireless LANs- Standards Activities in IEEE In IEEE Workshop on Local Area Networks, Worcester Polytechnic Institute, Worcester Massachusetts (pp. 58-63).
The 1st IEEE Workshop on Wireless LAN, Worcester, MA, May 9-10, 1991. http://www.cwins.wpi.edu/wlans91/index.html.
T. Wilkinson, T. G. Phipps and S. K. Barton, A report on HIPERLAN standardization, International Journal of Wireless Information Networks, Vol. 2, No. 2, pp. 99–120, 1995.
E. Ayanoglu, K. Y. Eng and M. J. Karol, Wireless ATM: Limits, challenges, and proposals, IEEE Personal Communications, Vol. 3, No. 4, pp. 18–34, 1996.
T. Liu, P. Bahl and I. Chlamtac, Mobility modeling, location tracking, and trajectory prediction in wireless ATM networks, IEEE Journal on selected areas in communications, Vol. 16, No. 6, pp. 922–936, 1998.
K. Pahlavan, A. Zahedi and P. Krishnamurthy, Wideband local access: Wireless LAN and wireless ATM, IEEE Communications Magazine, Vol. 35, No. 11, pp. 34–40, 1997.
Pahlavan, K. and Levesque, A.H., 1995. Wireless information networks. John Wiley & Sons.
Rappaport, T.S., 1996. Wireless communications: principles and practice. New Jersey: prentice hall PTR.
Khun-Jush, Jamshid, Peter Schramm, Udo Wachsmann, and Fabian Wenger, 1999. Structure and performance of the HIPERLAN/2 physical layer. In Gateway to 21st Century Communications Village. VTC 1999-Fall. IEEE VTS 50th Vehicular Technology Conference (Cat. No. 99CH36324), vol. 5, pp. 2667-2671. IEEE.
Doufexi, A., Armour, S., Butler, M., Nix, A., Bull, D., McGeehan, J. and Karlsson, P., 2002. A comparison of the HIPERLAN/2 and IEEE 802.11 a wireless LAN standard. IEEE Communications magazine, 40(5), pp.172-180.
K. Pahlavan, P. Krishnamurthy, A. Hatami, M. Ylianttila, J. P. Makela, R. Pichna and J. Vallstron, Handoff in hybrid mobile data networks, IEEE Personal Communications, Vol. 7, No. 2, pp. 34–47, 2000.
Hasan, S.F., Siddique, N.H. and Chakraborty, S., 2009, May. Femtocell versus Wi-Fi-A survey and comparison of architecture and performance. In 2009 1st International Conference on Wireless Communication, Vehicular Technology, Information Theory and Aerospace & Electronic Systems Technology, pp. 916-920. IEEE.
H. Zhang, Y. Dong, J. Cheng, M. J. Hossain and V. C. Leung, Fronthauling for 5G LTE-U ultra-dense cloud small cell networks, IEEE Wireless Communications, Vol. 23, No. 6, pp. 48–53, 2016.
Andrews, J.G., Ghosh, A. and Muhamed, R., 2007. Fundamentals of WiMAX: understanding broadband wireless networking. Pearson Education.
Jensen, M.A., 2016, June. A history of MIMO wireless communications. In 2016 IEEE International Symposium on Antennas and Propagation (APSURSI) (pp. 681-682). IEEE.
S. M. Alamouti, A simple transmit diversity technique for wireless communications, IEEE Journal on selected areas in communications, Vol. 16, No. 8, pp. 1451–1458, 1998.
V. Tarokh, N. Seshadri and A. R. Calderbank, Space-time codes for high data rate wireless communication: Performance criterion and code construction, IEEE transactions on information theory, Vol. 44, No. 2, pp. 744–765, 1998.
Alamouti, S. and Tarokh, V., New Cingular Wireless Services Inc, 2001. Transmitter diversity technique for wireless communications. U.S. Patent 6,185,258.
G. J. Foschini and M. J. Gans, On limits of wireless communications in a fading environment when using multiple antennas, Wireless personal communications, Vol. 6, No. 3, pp. 311–335, 1998.
Bianchi, G., 2000. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on selected areas in communications, 18(3), pp.535-547.
Wikipedia: IEEE 802.11: https://en.wikipedia.org/wiki/IEEE_802.11.
The Second IEEE Workshop on Wireless LAN, Worcester, MA, October 24-26, 1996 http://www.cwins.wpi.edu/wlans96/index.html.
MacWorld Keynote: Steve Jobs on Skyhook Technology (YouTube posting date: Jan 10, 2012) on https://www.youtube.com/watch?v=F624yzZ0Ysc.
K. Pahlavan, P. Krishnamurthy and A. Beneat, Wideband radio propagation modeling for indoor geolocation applications, IEEE Communications Magazine, Vol. 36, No. 4, pp. 60–65, 1998.
K. Pahlavan, Indoor Geolocation Science and Technology: at the Emergence of Smart World and IoT, Rivers PublishersThe Netherlands, 2019.
Bahl, Paramvir, and Venkata N. Padmanabhan, 2000. RADAR: An in-building RF-based user location and tracking system. In Proceedings IEEE INFOCOM 2000. Conference on Computer Communications. Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies (vol. 2), pp. 775-784. IEEE.
Li, X., Pahlavan, K., Latva-Aho, M. and Ylianttila, M., 2000, September. Indoor geolocation using OFDM signals in HIPERLAN/2 wireless LANs. In 11th IEEE International Symposium on Personal Indoor and Mobile Radio Communications. PIMRC 2000. Proceedings (Cat. No. 00TH8525) (Vol. 2, pp. 1449-1453). IEEE.
Prasithsangaree, P., Krishnamurthy, P. and Chrysanthis, P., 2002, September. On indoor position location with wireless LANs. In The 13th IEEE international symposium on personal, indoor, and mobile radio communications (Vol. 2, pp. 720-724). IEEE.
Kaemarungsi, K. and Krishnamurthy, P., 2004, March. Modeling of indoor positioning systems based on location fingerprinting. In IEEE INFOCOM 2004 (Vol. 2, pp. 1012-1022). IEEE.
K. Pahlavan, F. Akgul, Y. Ye, T. Morgan, F. Alizadeh-Shabdiz, M. Heidari and C. Steger, Taking positioning indoors - Wi-Fi localization and GNSS, Inside GNSS, Vol. 5, No. 3, pp. 40–47, 2010.
Mobility trends report, Apple Maps, https://www.apple.com/covid19/mobility .
Ye, Y., Akgul, F.O., Bardshady, N. and Pahlavan, K., 2011, April. Performance of hybrid Wi-Fi localization for cooperative robotics applications. In IEEE International Conference on Technologies for Practical Robot Applications (pp. 11-12).
Bargshady, N., Pahlavan, K. and Alsindi, N.A., 2015, February. Hybrid Wi-Fi/UWB, cooperative localization using particle filter. In 2015 International Conference on Computing, Networking and Communications (ICNC) (pp. 1055-1060). IEEE.
L. H. Chen, E. H. K. Wu, M. H. Jin and G. H. Chen, Intelligent fusion of Wi-Fi and inertial sensor-based positioning systems for indoor pedestrian navigation, IEEE Sensors Journal, Vol. 14, No. 11, pp. 4034–4042, 2014.
N. Bargshady, G. Garza and K. Pahlavan, Precise tracking of things via hybrid 3-D fingerprint database and kernel method particle filter, IEEE Sensors Journal, Vol. 16, No. 24, pp. 8963–8971, 2016.
N. Tadayon, M. T. Rahman, S. Han, S. Valaee and W. Yu, Decimeter ranging with channel state information, IEEE Transactions on Wireless Communications, Vol. 18, No. 7, pp. 3453–3468, 2019.
Pahlavan, K., Ying, J., Li, Z., Solovey, E., Loftus, J. P., and Dong, Z. RF cloud for cyber intelligence, IEEE Access, 8, pp.89976-89987.
Jakes, W.C., 1974. Mobile communication design fundamentals. John Wiley & Sons.
Pahlavan, K. and Matthews, J.W., 1980. Performance of channel measurement techniques over fading channels. In Proceeding of the IEEE NTC (Vol. 3, pp. 58-5).
Rahman, M.T., Tadayon, N., Han, S. and Valaee, S., 2018, December. LocHunt: Angle of Arrival Based Location Estimation in Harsh Multipath Environments. In 2018 IEEE Global Communications Conference (GLOBECOM) (pp. 1-6). IEEE.
Kotaru, M. and Katti, S., 2017. Position tracking for virtual reality using commodity Wi-Fi. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (pp. 68-78).
X. Wang, L. Gao, S. Mao and S. Pandey, CSI-based fingerprinting for indoor localization: A deep learning approach, IEEE Transactions on Vehicular Technology, Vol. 66, No. 1, pp. 763–776, 2016.
T. Roos, P. Myllymäki, H. Tirri, P. Misikangas and J. Sievänen, A probabilistic approach to WLAN user location estimation, International Journal of Wireless Information Networks, Vol. 9, No. 3, pp. 155–164, 2002.
Cheng, Y.C., Chawathe, Y., LaMarca, A. and Krumm, J., 2005, June. Accuracy characterization for metropolitan-scale Wi-Fi localization. In Proceedings of the 3rd international conference on Mobile systems, applications, and services (pp. 233-245).
A. W. T. Tsui, W. C. Lin, W. J. Chen, P. Huang and H. H. Chu, Accuracy performance analysis between war driving and war walking in metropolitan Wi-Fi localization, IEEE Transactions on Mobile Computing, Vol. 9, No. 11, pp. 1551–1562, 2010.
Fu, R., Ye, Y., Yang, N. and Pahlavan, K., 2011, September. Doppler spread analysis of human motions for body area network applications. In 2011 IEEE 22nd International Symposium on Personal, Indoor and Mobile Radio Communications (pp. 2209-2213). IEEE.
Y. Geng, J. Chen, R. Fu, G. Bao and K. Pahlavan, Enlighten wearable physiological monitoring systems: On-body RF characteristics based human motion classification using a support vector machine, IEEE transactions on mobile computing, Vol. 15, No. 3, pp. 656–671, 2015.
Pu, Q., Gupta, S., Gollakota, S. and Patel, S., 2013, September. Whole-home gesture recognition using wireless signals. In Proceedings of the 19th annual international conference on Mobile computing & networking (pp. 27-38).
Y. Ma, G. Zhou and S. Wang, Wi-Fi sensing with channel state information: A survey, ACM Computing Surveys (CSUR), Vol. 52, No. 3, pp. 1–36, 2019.
Z. Dong, F. Li, J. Ying and K. Pahlavan, Indoor motion detection using Wi-Fi channel state information in flat floor environments versus in staircase environments, Sensors, Vol. 18, No. 7, p. 2177, 2018.
Ali, K., Liu, A.X., Wang, W. and Shahzad, M., 2015, September. Keystroke recognition using Wi-Fi signals. In Proceedings of the 21st annual international conference on mobile computing and networking (pp. 90-102).
Z. Wang, B. Guo, Z. Yu and X. Zhou, Wi-Fi CSI-based behavior recognition: From signals and actions to activities, IEEE Communications Magazine, Vol. 56, No. 5, pp. 109–115, 2018.
L. Shi, M. Li, S. Yu and J. Yuan, BANA: Body area network authentication exploiting channel characteristics, IEEE Journal on selected Areas in Communications, Vol. 31, No. 9, pp. 1803–1816, 2013.
Shi, C., Liu, J., Liu, H. and Chen, Y., 2017, July. Smart user authentication through actuation of daily activities leveraging Wi-Fi-enabled IoT. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing (pp. 1-10).
He, Y., Chen, Y., Hu, Y. and Zeng, B., 2020. Wi-Fi Vision: Sensing, Recognition, and Detection with Commodity MIMO-OFDM Wi-Fi. IEEE Internet of Things Journal.
T. Aono, K. Higuchi, T. Ohira, B. Komiyama and H. Sasaoka, Wireless secret key generation exploiting reactance-domain scalar response of multipath fading channels, IEEE Transactions on Antennas and Propagation, Vol. 53, No. 11, pp. 3776–3784, 2005.
Mathur, S., Trappe, W., Mandayam, N., Ye, C. and Reznik, A., 2008, September. Radio-telepathy: extracting a secret key from an unauthenticated wireless channel. In Proceedings of the 14th ACM international conference on Mobile computing and networking (pp. 128-139).
R. Melki, H. N. Noura, M. M. Mansour and A. Chehab, A survey on OFDM physical layer security, Physical Communication, Vol. 32, pp. 1–30, 2019.
Shakiba-Herfeh, M., Chorti, A. and Poor, H.V., 2020. Physical Layer Security: Authentication, Integrity and Confidentiality. arXiv preprint arXiv:2001.07153.
Sheth, A., Seshan, S. and Wetherall, D., 2009, May. Geo-fencing: Confining Wi-Fi coverage to physical boundaries. In International Conference on Pervasive Computing (pp. 274-290). Springer, Berlin, Heidelberg.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Pahlavan, K., Krishnamurthy, P. Evolution and Impact of Wi-Fi Technology and Applications: A Historical Perspective. Int J Wireless Inf Networks 28, 3–19 (2021). https://doi.org/10.1007/s10776-020-00501-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10776-020-00501-8