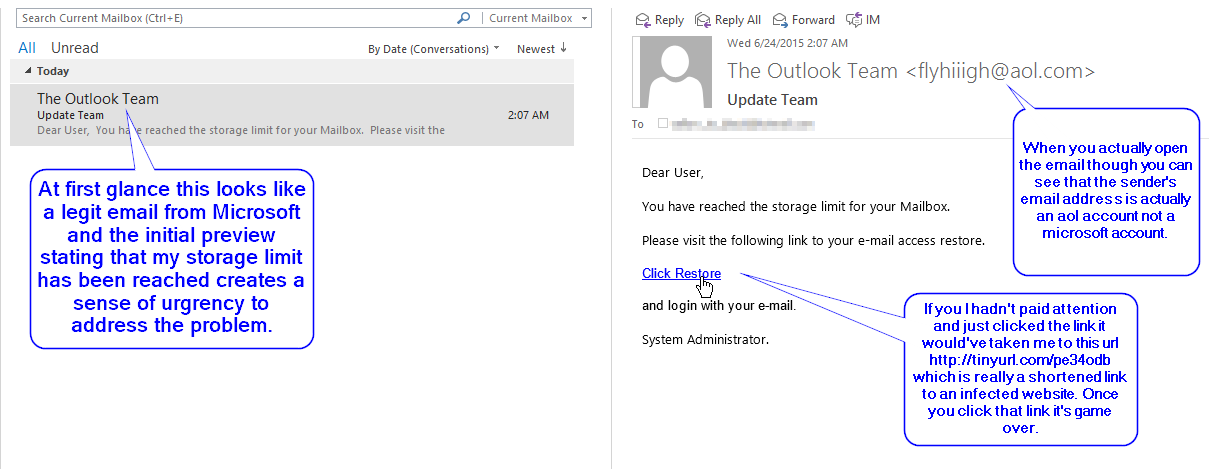
Here's a great example of a common way a virus gets onto your computer and into your network and how to guard against it.
Here at Bellingham IT we end up doing a lot of virus removals and clean ups and of course the end user always wants to know how the infection got onto their system. In reality, there are many different ways for a virus or other type of malware to get onto your system but here's a great example of one of the more common methods.This morning I was checking my inbox as usual and came across an email that stated it was from the Microsoft help team. A quick glance of the subject showed that my mailbox was full and needed attention right away. This immediately created a sense of urgency for me to address the issue but also threw up some red flags because I know that my mailbox has 15GB of storage space and shouldn't even be close to full.So I went ahead and clicked on the email to get the full message and scope it out further. Sure enough as soon as I saw the full message my red flags became clear indicators that this was not a legit email. First off the email address of the sender was from an aol.com account, obviously nobody from Microsoft is going to be sending official emails from an aol account. Secondly, the link that they wanted me to click was to a tinyurl site, not the kind of official Microsoft website address that you'd expect. Finally the email message itself was very basic and asked that after clicking the link that I sign in with my account credentials. Definitely not something I'd want to be doing. At this point I knew the email was bad news and so I deleted it.Here's a screenshot of my inbox and the email:  Here are some things that you can look for when suspicious emails like this hit your inbox.
Here are some things that you can look for when suspicious emails like this hit your inbox.
- Check the email address of the sender.
- In this case, I'm using Outlook and because the sender isn't in my contact list the email is displayed right alongside the sender name which makes it easy to see that it's not a valid microsoft email address. In other email clients like Apple Mail, Thunderbird, iOS Mail etc... they will sometimes not display the email address and only show the sender name (which is easily changed to be whatever a sender wants). To actually see the email you can usually click or hover over the sender's name and the real email address should appear.
- Check the actual URL of any link before actually clicking on it.
- Before clicking on anything in a suspicious email always check to see where it's going to be taking you. In my example, all I had to do was hover over the link and the real url popped up showing me that I would be headed to a tinurl if I clicked it. If you are unsure of how to check the url before clicking on it talk to your IT resource and ask them to help you out. If they're not available it's better to not click anything at all and report the email.
- Use the email body to help determine legitimacy.
- In this example you can see that the email is very basic and doesn't really look like something that would come from Microsoft. This is a helpful indicator that it's probably not a legit email. Use caution however when judging an email based on it's looks. Many malicious emails can actually look very professional but still be misleading. Usually I use an email body as further means of incrimination when I've found the first two points made above to be valid.
- If you're unsure about an email, ask your IT resource before doing anything.
- This is probably one of the most critical things you can do. If you've recieved a suspicious email and have gone over the steps above and you're still unsure, reach out to someone that's an expert on the matter. Cleaning up after a virus or infection costs hundreds of dollars at best and thousands at worst! It's much better to practice the ounce of prevention rule here. Trust me when I say you do NOT want to be the person that just infected the entire organization with cryptolocker!
Hopefully this example helps raise your level of awareness around what a malicious email can look like and how you can recognize them in the future. If you ever have any questions, we're happy to help. Want Bellingham IT blog updates to hit your email? Click here to subscribePhoto Cred: Bellingham IT